A security researcher has just published a new, proof-of-concept attack that allows thieves to unlock and steal a Tesla Model Y. Josep Pi Rodriguez, a principal security consultant with IOActive, identified the potential exploit and, while it might be tricky to pull off in the real world, it shows how cars underpinned by advanced technology can also be vulnerable to novel attacks.
A Tesla Model Y can be legitimately unlocked in three ways: With a keycard that uses near field communication (NFC), with a correctly configured smartphone, or with a key fob (that is a $175 add-on). This attack—called an NFC relay attack—targets the Tesla’s keycard system.
Before looking at how the hackers exploit this vulnerability, let’s step back and understand how the keycard system works. Tesla provides two smart keycards with every car. They are required to set up the smartphone-based key, and Tesla recommends that drivers keep a keycard in their wallet at all times as a backup in case their phone breaks or runs out of battery, or Tesla’s servers go down. (As futuristic as unlocking your car with a phone is, getting stuck somewhere because you dropped your device in the toilet is not exactly Jetsons material.)
To unlock their car, drivers hold the keycard up to the middle B-pillar. The car detects the nearby card and issues a cryptographic challenge over NFC. The smart keycard calculates the correct response and replies using NFC. The car validates the response and opens the doors. The driver then has two minutes to start the car and drive off before the keycard needs to be validated again. This is the process that the NFC relay attack seeks to break.
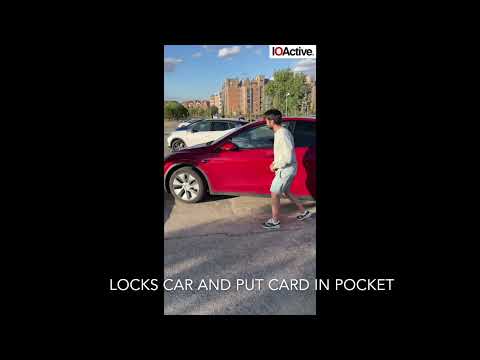
To pull it all off, the relay attack requires two thieves working together. One stays close to the car with a device called a Proxmark that is capable of imitating NFC devices, while the other has to get close to the target’s keycard with a NFC reader equipped smartphone. The Proxmark and the smartphone communicate over Bluetooth or Wi-Fi. You can see it in action in the video above.
Of course, developing the attack was a little more complex. Rodriguez had to decipher the Tesla’s communication protocol in order to accurately emulate it. If you want to see the low-level code, he breaks it all down in the research paper.
Also, it’s worth mentioning that this is all just a proof-of-concept. While thieves have taken Teslas with relay attacks in the past, there are still a number of challenges that they would face pulling this method off in the real world. First, the attackers have to find a target that carries their keycard in a predictable pocket. Second, they have to get a smartphone or other NFC-reading device close to the target’s keycard without them noticing—possibly while they’re standing in line for coffee or are otherwise stuck in a queue. Finally, the two attackers currently have to be within Bluetooth or Wi-Fi range of each other, so the target is still going to be pretty close to the car.
Of course, there are ways to overcome some of these challenges for a motivated hacker. Rodriguez theorizes that the range of the NFC-reading device could be increased from around 2 inches to around 2 feet. Similarly, the Wi-Fi range of the Proxmark can be increased using a Raspberry Pi as a wireless relay. He also thinks it is possible to perform the attack using an internet connection.
Once the car is unlocked, the attacker can hop in and drive off. They aren’t able to restart the car if they stop the engine, so they are most likely going to sell it for parts or steal any valuables left lying around.
If you own a Tesla—or any other car that uses an NFC keycard—you should be aware of this attack, but not overly concerned. This is the kind of thing that can only be pulled off if you are specifically targeted. Regular Tesla drivers going about their business are unlikely to be at much risk.
With that said, there are still a number of steps you can take to mitigate the attack. Enabling Pin-to-Drive would prevent the attackers from being able to drive off. You could also keep the keycard in an RFID-blocking sheath which would prevent it from being read while you stand in line for your coffee.
Overall, Rodriguez thinks that Tesla has a good security track record. In an interview with The Verge, he says, “Tesla takes security seriously, but because their cars are much more technological than other manufacturers, this makes their attack surface bigger and opens windows for attackers to find vulnerabilities.” In other words, as cars get more like computers, hackers have way more options in how they can attack them. There may not be a need for crowbars any more.