Computer scientists are developing a ‘master’ fingerprint that could unlock your phone
But questions remain

Fingerprint readers, like the TouchID on an iPhone, exist to make your device extra secure while keeping the process of unlocking it easy. Computer scientists at New York University and Michigan State are poised to turn that security benefit on its head. Like a master key that can open any lock, these researchers developed digital “master prints” that could emulate a variety of partial fingerprints enough to hypothetically hack into a device.
The researchers wondered if there was a fingerprint equivalent to a common four-digit security code, like “1234.” Using analysis from a digital database, they discovered that, indeed, a master print could successfully mimic a random fingerprint 26 to 65 percent of the time, according to the study. Why such a huge range? It depends on the scale of the fingerprint database; the more partial fingerprints enrolled in a fingerprint sensor system, the greater the chances are that a master print could unlock it.
There are several security issues at play. One, fingerprint sensors on smartphones are usually small, and two, a user can enroll multiple fingers. What’s more, a phone usually gives you several attempts to unlock it with your print.
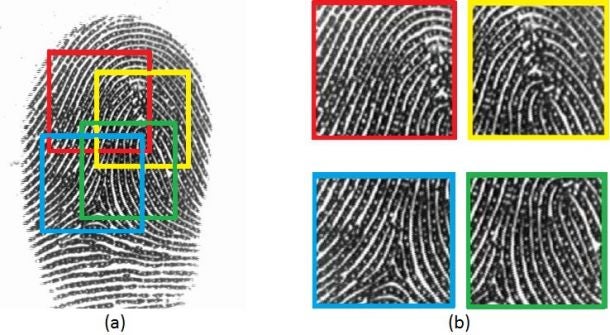
“The sensors are small and they don’t capture the full fingerprint,” says Nasir Memon, a computer scientist at NYU’s Tandon School of Engineering and one of the authors of the study.
And since a smartphone fingerprint sensor can be taught to recognize several different fingers, the system learns a lot of partial prints. When you place a finger on the sensor, the system doesn’t actually know which finger it is, or how you’re positioning it.
“So if any one of them match,” he says, “it will say ‘okay, that’s you.’”
Memon and his colleagues analyzed a digital database of 800 fingerprints, then extracted thousands of partial prints from that same database.They wondered: Are there any partial prints that match the others with a high probability? “We were surprised,” he says, “there were some that match like 15 percent of the time.”
It’s worthwhile to note that the experiment was computer-based, so the researchers did not try to actually trick phones using a master print. The findings are theoretical, and one prominent biometrics researcher is skeptical.
Anil Jain, the head of the Biometrics Research Group at Michigan State University, who was not involved in the study, says the researchers used a system that analyzed fingerprints based on an element of your print called “minutia.”
If you look at your finger, you’ll see lines of ridges and valleys. In some places, a ridge splits, or bifurcates. In other places, a ridge might simply end. Those ridge bifurcations and endings are what biometrics experts call “minutia points.”
Jain says fingerprint sensors used by Apple and Samsung do not use these minutia points to identify a print. Instead, the TouchID sensor on your iPhone, for example, is using the “texture pattern” of your print, Jain says.
Still, the study’s co-author, Arun Ross, a professor of computer science and engineering at Michigan State University, stands by the relevance of their findings. The vulnerabilities of the system remain: as fingerprint sensors get smaller, “the chances of my fingerprint matching with your fingerprint,” he says, “not in its entirety, but in portions of it, increases.”
