Big Brother 101
Could your social networks brand you an enemy of the state?
Hub Bubs
Instant Expert:
By some counts, government snoops are sifting through data from a billion or more phone calls and online messages daily. What might they be looking for?
- WHO: The National Security Agency and other intelligence groups
- WHAT: Processing and connecting data from phone calls, e-mails, online postings and financial transactions
- HOW: Using social-network analysis (the study of how people interact) and data-mining techniques (such as pattern-recognition algorithms) first used for artificial intelligence and consumer marketing
- WHY: To help uncover the structure of potential terrorist groups-far too secretive and dispersed to locate with traditional detection techniques-and decode their intentions
FAQs
Does this stuff REALLY work?
Data-mining techniques regularly help investigators identify credit-card-fraud and money-laundering patterns. And research in 2002 by social-network-analysis pioneer Valdis Krebs showed how the 9/11 plotters were all linked (some hijackers were separated by as many as 10 degrees, he found), but that was, alas, after the fact. Predictive data mining to preempt terrorist networks or activities hasn´t been publicly proven so far.
Why would the feds want my phone records?
To cast the widest possible data net. What seem like coincidental events can offer hidden ties. If person A makes a phone call to person B, and half an hour later person C transfers $10,000 to the account of person D, all four of them could be in the same gang (or not). Analysts also chart what terrorists have done in the past-phoning Afghanistan, cashing checks from Saudi Arabia, enrolling in flight school, buying fertilizer-to sniff for people who might fit similar pattterns now. Yet predictive software must be “trained” with good sample data or the algorithm might not work (witness 2002´s “terror pizza” mishap: the idea that repeatedly ordering a pie with a credit card somehow indicated enemy-of-the-state status). Some data miners believe that just about everyone has to be included because you don´t want to chance missing anybody in that huge pool of American averageness.
So what´s the big stink all about?
Besides, um, the Constitution? Intelligence pros themselves argue fiercely over how widely to look for suspects. Some say all that extra data is merely noise that too often sends the feds running down the wrong paths. Better to start data-diving with known perps, insists Naval Postgraduate School counterterrorism expert John Arquilla: “Pulling on a string, instead of just casting a net to see what comes up.”
Continue on to the next page to see how social networks can uncover the true mastermind of a group.
Uncovering the True Mastermind
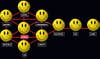
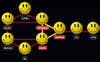
Who´s the most important player in a group? Who´s merely peripheral? Data crunchers find out by plotting people as “nodes” on computerized graphs, forming web-like networks. The links between nodes are then weighed and analyzed using matrix algebra and other tools.
How close are you and your cellphone records to a terrorist? If the whole country is your potential database, finding the answer might seem like Six Hundred Degrees of Separation. Investigators measure these three qualities when assessing any links:
- Connectedness
In the simplified network [below] developed by Carnegie Mellon´s David Krackhardt, Diane is the hub with the highest â€degree centrality,†gauged by dividing the number of nodes (people) reached by the total nodes in the network. Diane looks like the key. But take her out, and communication still flows. 2. Betweenness
The real heavy hitters are often the brokers who bring together different constituencies. They have the highest degree of “betweenness,” measured by the number of times communications must pass through someone on the network. Heather, for instance: If you were to remove her from the network, the right side couldn´t communicate with the left. If this were an Al Qaeda cell, she´d be the one to lock up. 3. Closeness
The number of times people are on a geodesic-the shortest possible path between two others-is also vital. These direct connections allow them to reach a maximum number of nodes in a minimum number of steps. In this group, Fernando and Garth can monitor (and control) information passing through the network. Everyone else is basically playing the game “telephone,” with one person giving another a message, and so on, degrading communications at each step. Fernando and Garth more or less skip the game and talk to people directly, so they´re better informed. If you´re looking to eavesdrop, “close” people, like Fernando and Garth, would be your best bets.

Hub Bubs
Heads Up
_
What’s it take to get on the list? Click here to read one PopSci staffer’s story._