The World’s Most Sophisticated Malware Ever Infects Hard Drive Firmware
High-tech "Equation group" is likely connected to NSA
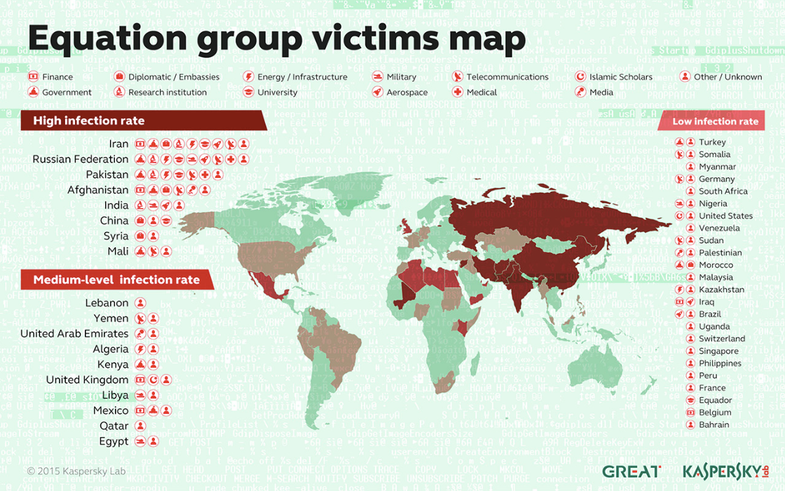
There’s a new malware king on the block. Security researchers at Moscow-based Kaspersky Labs have uncovered a sophisticated suite of software packages that stem from what it calls the “Equation” group, a single cluster of unidentified hackers dating back to 2001.
A few things point to involvement by the U.S. intelligence apparatus: the complexity of the software; the groups and organizations targeted by the code; and similarities with known malware like Regin, Stuxnet, and software mentioned in documents from Edward Snowden. It’s most likely the work of the National Security Agency (NSA), but Kaspersky doesn’t explicitly draw that connection.
The malware can rewrite the firmware of hard drives–i.e. the very software that controls a device–making it virtually impossible to detect, let alone remove.
What makes Equation’s work so impressive is the lengths to which it will go to infect target computers. In a never-before-seen capability, its malware can rewrite the firmware of hard drives–i.e. the software on the devices that controls them–making it virtually impossible to detect, let alone remove. Such an exploit would require access to private source code from hard-drive makers, though several of those companies denied to Reuters any knowledge or involvement.
The Equation group might also use a technique called “interdiction,” in which they intercept mailed goods and replace them with infected versions; in one instance, Kaspersky learned CDs mailed to attendees of a scientific conference were replaced with versions containing one of Equation’s Trojan horse programs.
The news has the feel of some dark web, Big Brother-esque conspiracy, but does this directly impact you, the average computer user? Probably not. For one thing, the Equation group’s software appears to be highly targeted. It uses what’s called an “escalation model:” a Trojan horse first determines whether or not the target is of interest before installing more invasive software. Much of the malware is also designed to self-destruct after a period of inactivity–no doubt intended to cover its tracks. But in one particular exploit of an online forum, Equation’s exploit went out of its way not to track or infect unregistered users, targeting only those who were logged in.
Even if you are concerned about being infected by the Equation group’s malware, there’s little to be done about it at present. The software is so sophisticated that techniques to remove it don’t yet exist–but we expect Kaspersky and other vendors will work to identify those methods.